News hit the internet Friday when IT Security Firm VT Trust announced major security flaws in Yealink's Redirection Service. Yealink is now the number 1 global manufacturer of VoIP phones edging out Polycom.
What is a reduction service exactly?
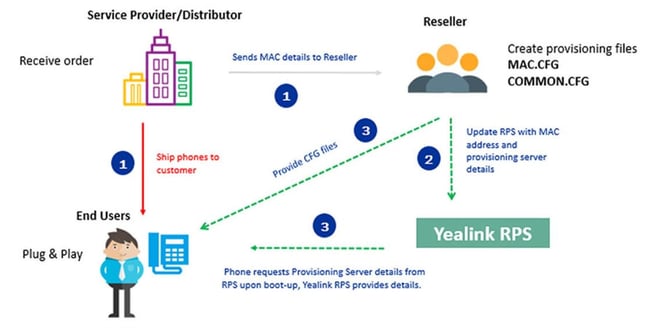
To sum up the diagram above, most VoIP device and IOT companies have a "call home protocol," which when a device is brand new out of the box or factory reset and the device is connected to the internet, it connects to a manufacturer server to see if instant provisioning information is available so that devices don't need to be manually touched to setup a configure each time before they get deployed out in the field.
So, imagine you are rolling out a new phone system, phone service provider, meeting room system, or even Microsoft Teams and you or your provider has utilized the Yealink RPS for instance provisioning, what will get exposed is the provisioning URL that the phones need to download its unique profile to connect to the service of your choice.
So, WHY is this security flaw a problem?
Well, if someone where to gain access to download the profile that gets downloaded to a device to register to phone system, in this case then usernames, server IPs and Fully Qualified Domain Name (FQDNs), and all the other things required to make a phone work properly would then be exposed in many cases. Once someone has this information, it can be exploited to do bad things.
- In phone system / provider land, this leads to what usually starts as fraudulent calls or toll fraud that can rack up quite a big phone bill.
- Other things could be exposed such as access to voicemails, company directories, call logs, call recordings, and so on, which are problematic in their own right, especially in industries with regulations around this type of data being exposed.
One tactic we have seen in the past....
Once a provisioning directly the houses profiles for several devices is exposed, someone can sequentially go up in the mac address range for any manufacturer until they get positive hits in a brute force style way. These attempts are as simple as taking any web URL, dropping it into a browser address bar and then sequentially changing the address by one character. Of course, if scripted this type of attack can take days, weeks, or months until positive hits are returned. Since this is not an authentication attempt a lot of systems out there don't have adequate security measures for this.
OK. So, no big deal... change the URL, or IP address, credentials, and move on.
Well, not so fast. First, that may not be very easy to do especially when you may not control the backend systems to make this change. Second, the MAC address of a phone is not something that can be changed! It is a permanent thing unless you plan to replace one or all of your devices. So, what do you do? Delete your RPS entries, re-configure / redeploy the backend system, and manually reconfigure all of your phones?
Thoughts
Each service provider needs to do extra things to help protect this from causes larger issues if they have not already.
Here at bvoip we have multiple ways to help avoid an attack of this nature.
Provisioning Platform that sits in front of the actual VoIP system
Instead of pointing a RPS system directly to the UC, VoIP, or Phone System directly, bvoip has a provisioning platform that enforces certificate checking, which means that the system will deny the ability for something other than the device belonging to the MAC address to download its profile.
In a future update, you can even narrow which IP addresses you switch provisioning pulls to come from in lieu of certificate checking to lock down where request can come from even further.
VoIP / PBX Security Measures
In 2018, bvoip released Barricade for all of our partners free of charge. This is bvoip's approach to limiting access to access any particular account or system to only known devices or IP address. This is 2-factor approach to VoIP security, which many systems don't have an answer for out there.
If an attacker is never able to access a provisioning director or be able to access the system itself, then likely they will move on to other targets without security measures in place!
What's going to happen at Yealink?
We have already seen unannounced changes pop up, which could change the way Yealink allows its RPS to be accessed and used. We don't know the full extent of these changes or how we will need to react to be able to work with their redirection service. So far, the early changes seem to be that Yealink is going to limit phones to only access its RPS from one IP address. That may cause an issue if phones are being deployed out in the wild behind dynamic IP addresses and needed to be re-provisioned for whatever reason. Time will tell how things will work moving forward.